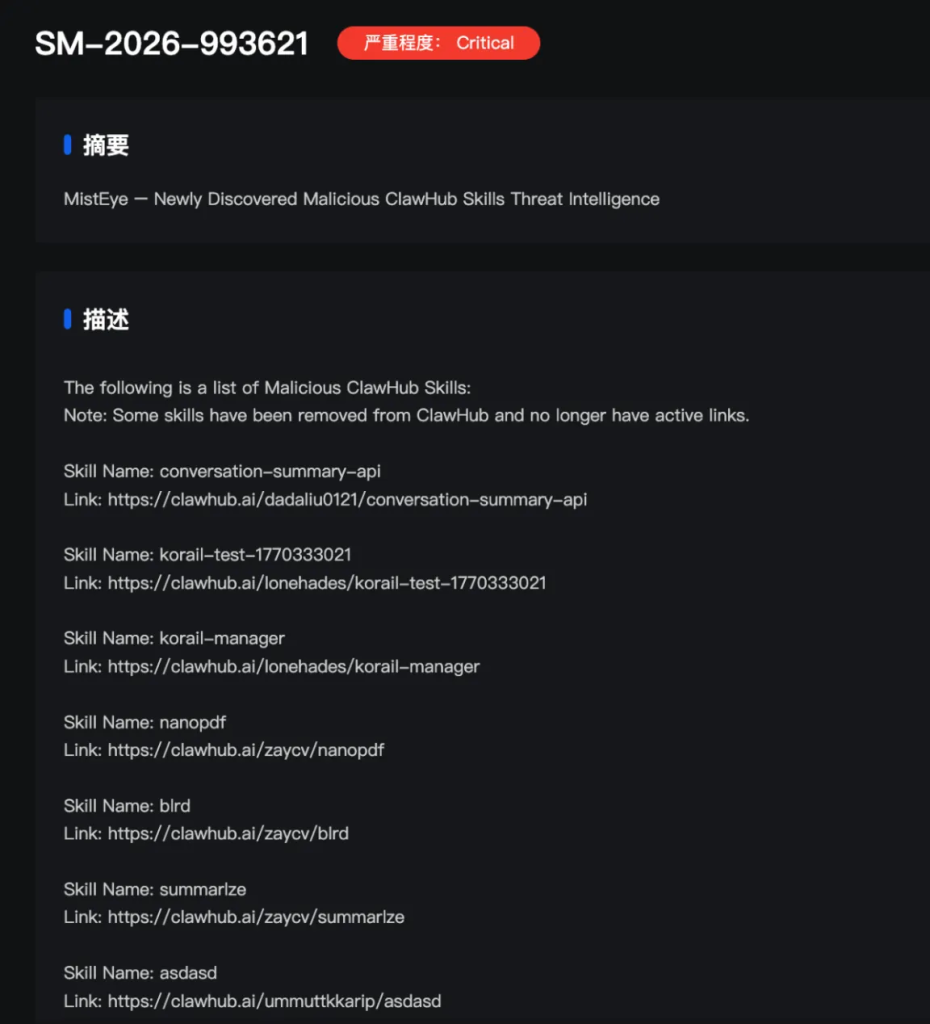
The official plugin marketplace for open-source artificial intelligence agent project OpenClaw has become a target for supply chain poisoning attacks, according to a new report from cybersecurity firm SlowMist.
In a report released Monday, SlowMist said attackers have been uploading malicious “skills” to OpenClaw’s plugin hub, known as ClawHub, exploiting what it described as weak or nonexistent review mechanisms. The activity allows harmful code to spread to users who install the plugins, potentially without realizing the risk.
SlowMist said its Web3-focused threat intelligence solution, MistEye, issued high-severity alerts related to 472 malicious skills on the platform.
Supply chain poisoning is a cyberattack where hackers infiltrate a software supplier or component to inject malicious code before it reaches the end user.
Related: DOJ-released emails suggest Epstein made $3.2M Coinbase investment in 2014
Malicious skills hide backdoors
According to SlowMist, the infected skills masquerade as dependency installation packages, which hide malicious commands that trigger backdoor functions after being downloaded and executed, a tactic the company compared to a Trojan horse.
Once installed, the malicious actors typically resort to “extortion following data theft,” according to SlowMist, as the “Base64” backdoor can collect passwords and personal files from infected devices.
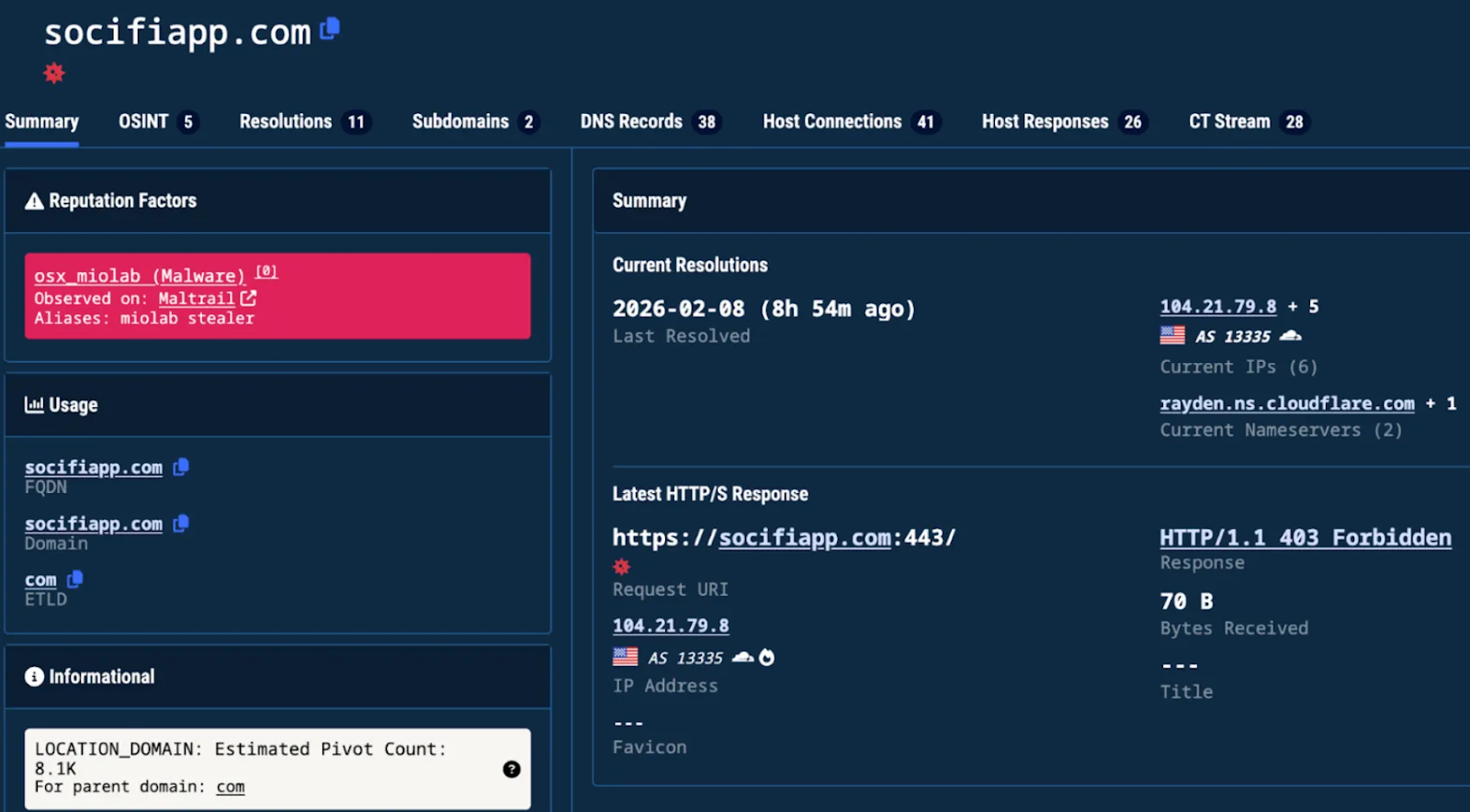
Most of the attacks stem from the same malicious domain address (socifiapp[.]com), registered in July 2025, and the same IP address associated with Poseidon infrastructure exploits.
Related: Whale’s $9B Bitcoin sale was not due to quantum concerns: Galaxy Digital
The malicious skills were frequently named using terms associated with crypto assets, financial data and automation tools. These are categories that SlowMist said are more likely to lower users’ vigilance and encourage quick installation.
SlowMist’s findings point to a greater coordinated effort by an organized group, as multiple infected skills point to the same domains and IP.
“This strongly suggests a group-based, large-scale attack operation, in which a large number of malicious skills share the same set of domains/IPs and employ largely identical attack techniques.”
Cointelegraph has contacted SlowMist for additional details on which crypto-related AI skills were most heavily targeted.
In a Feb. 1 report, cybersecurity firm Koi Security also flagged that 341 out of the 2,857 analyzed AI skills contained malicious code, reflecting a typical pattern of supply chain poisoning attacks through plugins and extensions.
To avoid falling victim to this threat, SlowMist recommends that users first audit any SKILL.md sources that require installation or copy and paste execution. Users should also be suspicious of prompts that require system passwords, accessibility permissions or ask to execute system configuration changes.
Magazine: Meet the onchain crypto detectives fighting crime better than the cops